I worked hard to get rid of your computer and worked hard to compress your files. I work overtime, so desperately, if you don't give money, you want to return your password. Is there such a reason? Don't you feel ashamed in your heart? Isn't your conscience not tormenting? Not convinced to argue! This is probably the inner monologue of "blackmail hackers."
In fact, since 2015, hacker extortion has become a mainstream black industry. What makes people angry is that after a few years of vigorous development, the industry has actually split its genre.
" Academic"
"Academic" is the most traditional and most popular blackmail hacker. They use "independent development" encryption software to remotely attack your computer and then encrypt all important files to form a batch of ".locky" or similar strange extension files. The way to pay the ransom will then be displayed on the desktop. Do not say that ordinary people, even security experts are difficult to decipher.
Such ransomware mainly faces corporate executives or celebrities. The reason is simple, because the files on their computers are often more valuable, and the rich are willing to pay more for their private documents. Under normal circumstances, hackers will extort bitcoins worth more than $2,000 depending on the situation.

The interface popped up after being blackmailed
"Technology genre"
Such hackers are masters of swords on the basis of "academics". Their extortion targets are generally organizations such as hospitals, schools and churches.
In February 2016, hackers attacked a hospital in Los Angeles, locked all computers, and the hospital could only work with paper and pencil. The extremely low efficiency and the loss of cases have caused a large number of patients to say that they will never come to this hospital again. The hospital eventually paid an equivalent bitcoin ransom of $17,000.
Also in February 2016, hackers continually attacked two churches in the United States, locking in important information, and after paying a $570 equivalent of a bitcoin ransom, everything returned to normal. The church's pastor said that the $570 is nothing, the key is that he has never used Bitcoin. After this blackmail, the old pastor who was not so computerized was forced into a technical house by a hacker. The success rate of such ransomware is extremely high, because no hospital and school can withstand the tossing of business.
"Kindergarten School"
Recently there has been a wonderful genre, that is, "Kindergarten School." The target of such hackers is ordinary people like you and me. Of course, because of the face of the majority of Diors, the charges are naturally "civilian standards": as long as 0.32 bitcoin (equivalent to 900 yuan). Because it is a "small business" for civilians, the hacker's blackmail technology is actually a "small version."
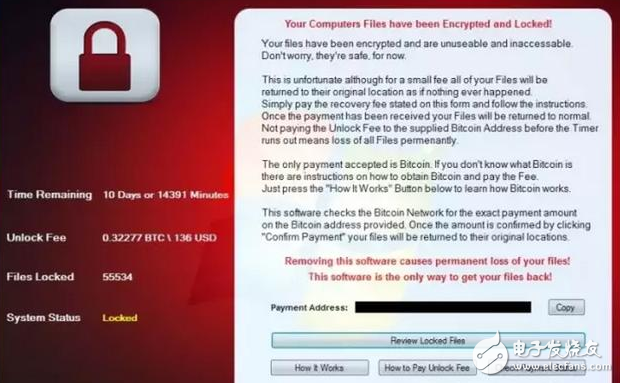
The blackmail letter shows that unlocking the file requires 0.32 bitcoin ($136)
So what kind of method does this "Kindergarten" hacker use to engage you? Recently, experts from many security teams have declassified a hacker organization's ransomware technology:
Hackers transfer ransomware to their personal computers through phishing sites, just like traditional hackers. However, because they don't have dedicated encryption software, they have to adopt a soil approach: put important files into the RAR archive and set a password. If you want to extract these zips, you need to "buy" the password back from the hacker.
Although the method is simple, it looks seamless. However, security experts have found through research that in fact, if you want to know the decompression password, you don't need to buy it from a hacker.
The hacker calculates a string of characters from your "processor ID number", "board serial number" and "system disk volume serial number". This string of characters is the file name of the compressed file. But it seems that NB's shiny file name is not really important. You only need to add your own Windows username after the file name, and "calculate" to understand the password.
for example
If the name of the compressed file is "1A2B3C" and the Windows user name of this computer is "leiphone", then the decompression password is: "1A2B3Cleiphone".
(Since the decompression password is "file name" + "username", then what is the use of this gorgeous file name generated by the hacker brother computer parameters?)
The security researcher racked his brains and eventually found that the compressed file "Ecstasy" was so good. But the hacker is not as low as you think, even if you know the secret of the password, you may not be able to extract it. Because the hacker puts an eyeliner in your computer - a process called "cryptohost.exe". After manually closing this process in Task Manager, you can happily unpack your favorite files.
At present, the mainstream anti-virus software can already kill the "Kindergarten School" extortion Trojan. However, children's shoes must be careful and careful when clicking on unknown links. Because the day is not allowed, the kindergarten hackers will grow up. . .
Multifunctional Operating Device For Alps Automobile
Push-Operated Switch,Multi-Function Switch Used By The Camera,Operation Switch For Health Products,Multifunctional Operating Device For Alps Automobile
DA CHENG MINGHUA LIMITED , https://www.alpsswitch.com