While cloud computing technology provides users with versatile and personalized services, it is also easy to cause users' private data to be leaked. The application provider stores the data information in the data center of the third-party cloud computing service provider, and the user accesses the data information by using various third-party excuses provided by the cloud computing service provider. In the process of data access, cloud computing service providers play a very important role, which has a direct impact on the security of user privacy data. In the cloud computing application service mode, user privacy data is quite different from traditional personal privacy information. How to effectively protect the security of users' private data is a challenge in the information security field. How to ensure that user identity will not be leaked and stolen by cloud computing service providers has become an urgent problem in the field of cloud computing security.
This paper addresses the common data privacy leakage problem in cloud computing application services, using public cryptography based on user identity, combined with secret sharing strategy to ensure the security of user privacy data, and the newly added user identity will not cause new private data leakage. It has the characteristics of high performance, low cost and low energy consumption.
1. User Identity Encryption Technology (IBE)
Faced with the information security threat brought by the CA certification center in the traditional security authentication system, the user identity-based encryption algorithm can be used to prevent it. The user identity-based encryption algorithm was originally designed to solve the impact of the CA certification center on the email authentication system, to ensure the uniqueness of the email name in the email system, and to use the algorithm strategy to convert the string into a public corresponding to the user. The key avoids the disadvantages of re-interacting with the CA certificate center when the user needs to use the public key of another user, and reduces the workload of the key management center. The private key is transmitted to the corresponding user through a secure channel. Thus, the workflow of the encryption algorithm based on the user identity is shown in Figure 1.
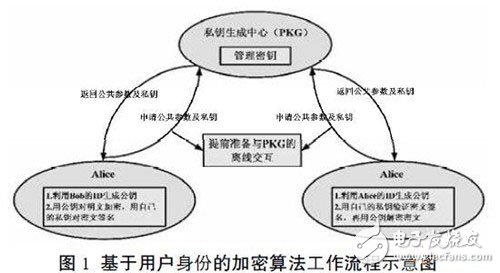
The encryption algorithm based on user identity mainly includes two special advantages: First, when the user transmits ciphertext with other users, data encryption can be realized without data interaction with the key management center, and only the target user can The ciphertext is decrypted and viewed. Secondly, in the data encryption process, the user identity definition work is simple and fast, and only a string of unique characteristic characters can be used to realize the difference of the user identity, thereby ensuring the uniqueness of the user public key.
2. Construction of cloud computing data privacy protection scheme based on IBE
2.1 User Authorized Access
In the cloud computing environment, the data provider can use the security parameter generator in the IBE encryption policy to effectively control the user's permission to upload data information. The data information is encrypted according to the user's public key. Therefore, only the user corresponding to the public key can obtain the encrypted data information through the personal private key. However, the encryption of all the data information by using the IBE-based encryption policy consumes a large cost. Usually, only the IBE is used to encrypt key data information, such as user personal identity privacy data, user uploaded data geographic location, and the like. Moreover, in the cloud computing service providing platform, the user identity should be uniformly authenticated and managed to ensure that each user has a unique identity. Thus, the data provider can implement authorization authentication for the cloud computing service provider. Whether it is a cloud computing service provider approved by the data provider, or a cloud computing service provider that cooperates with it, as long as the data provider does not authorize it, even if the cloud computing service provider obtains encrypted data information, data decryption cannot be achieved. .
2.2 Data Fault Tolerance Recovery
The secret sharing strategy mainly uses the polynomial to divide the secret into N parts, and at the same time sets the threshold k(N"k). As long as the user has a share of k or more, the secret can be restored. In the secret sharing policy, the secret may be data location information, user identity information, or a string of data keys. Generally, the secret share is distributed in the storage space provided by the cloud computing service provider. As long as the storage space of the untrusted cloud computing service provider is less than Nk, the service provider cannot crack the secret, thereby improving the security of the user's personal privacy data. Sex. At the same time, the secret sharing strategy can satisfy the distributed characteristics of cloud computing technology. As long as the correct number of secret shares is greater than k, the original secret can be reconstructed, and thus the user can obtain correct personal privacy data.
2.3 Authorization Data Verification
In order to ensure that the data information used by the cloud computing user is derived from the encrypted data uploaded by the data provider, it will not be cracked by the outside illegal intruder during the data transmission and storage process. Therefore, the data verification link can be introduced in the secret sharing strategy. The secret sharing strategy is verified. The scheme must require the data provider to use the unique information to sign the data information after the data encryption is completed. When the legitimate user needs to access the data, it must be digitally signed to ensure the security and integrity of the encrypted data. Sex.
Therefore, the privacy data security solution proposed in this paper consists of four steps: system initialization, secret distribution, secret share verification, and secret reconstruction. The specific protection scheme is shown in Figure 2.
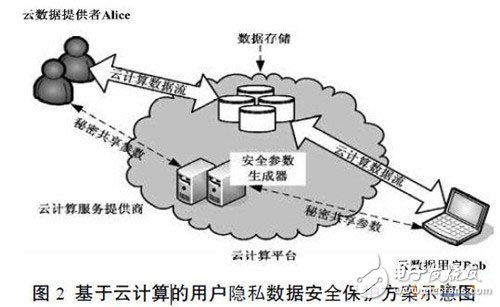
3, the conclusion
The protection of cloud computing user privacy data is different from traditional user data security. Because cloud computing technology has distributed characteristics, its boundaries are also vague, and cloud computing service providers have open space and easy environment, thus effectively solving cloud computing. The user privacy data protection problem in service providers is very important. The IBE-based cloud computing data privacy protection scheme proposed in this paper can ensure that user privacy data is not leaked and has a good application prospect.
Tree Lighting Nyc,Led Tree Lightning,Tree Lights Wedding,Commercial Christmas Light
XINGYONG XMAS OPTICAL (DONGGUAN ) CO., LTD , https://www.xingyongxmas.com