Keywords: network, architecture, characteristics, plan
1 Introduction At the end of the 1990s, with the in-depth application of network technology in various industries, the IT industry has emerged a new architecture with low costs, low management overhead, and the advantages of the Client / Server computing model-the three-tier network Architecture. If the C / S architecture is called "fat client / server" computing mode, then the three-tier architecture can be called "thin client / server" computing mode.
2 Technical characteristics The three-layer (or multi-layer) structure is characterized by adding one (or more) middleware layers on the basis of the two-layer structure. It moves the application program originally running on the client to the middleware layer in the C / S architecture. The client is only responsible for displaying the interface with the user and a small amount of data processing (such as data legality verification). The client submits the collected information (request) to the middleware server, and the middleware server performs corresponding business processing (including operations on the database), and then feeds back the processing result to the client.
Compared with the traditional C / S architecture, the three-tier architecture has the following advantages:
2.1 Zero client maintenance In the three-tier architecture, almost all business processing is done on the middleware Web Server, the client only needs to install a browser that supports Java, without any other installation and configuration Work, so there is no problem of client maintenance, and truly achieves "zero client maintenance". When processing business, the operator can directly access the Web Server through a Web browser to perform business processing work.
2.2 Good scalability The scalability of the three-tier architecture is reflected in the following four aspects:
First, the scalability of the working node is good. Due to the zero-maintenance characteristics of the client in the three-tier architecture, the task of adding a working node is as simple as adding a PC with a Web browser.
Second, the scalability of the application system is good. A good application system should be able to easily realize the change of business and the increase of business units to a certain extent. The three-tier architecture adopts object-oriented analysis and design patterns, encapsulating business modules into business classes and service classes, so if a business process changes, or a new business module needs to be added, just replace or add a new one Business class and service class.
Third, the business logic is separated from the user interface and database, so that when the user's business logic changes, it is only necessary to change the controls / components / JB / EJB in the middle layer.
Fourth, it is convenient for database migration. Since the client does not directly access the database, but through an intermediate layer, there is no need to change the client configuration when changing the database, driver or storage method, as long as the database connection part of the persistence layer on the middleware is changed collectively can.
2.3 Good security In the three-tier architecture, the client can only directly access the database through the Web Server, which greatly improves the security of the system. If higher security requirements are imposed on the system, it can also be shielded through a firewall.
2.4 Good resource reuse Because the business logic is centralized to Web Server for unified processing, the three-tier architecture can make better use of shared resources. For example, a database connection is an event that consumes system resources and affects response time. In a three-tier architecture, the database connection can be managed in a buffer pool for unified management, shared by different applications, and effectively controlling the number of connections.
3 Composition structure The three-layer structure is mainly composed of the following three parts:
3.1 Client The main task of the client is to display the user interface and receive user events. In the three-tier architecture, the user interface is displayed through the browser, and the WebServer will download the response to the client browser using HTML as the carrier. After the browser (such as IE, NetScape) interprets, the final user interface is obtained. From a technical perspective, the client program consists of the following parts:
3.1.1 HTML
HTML is the carrier of all interface elements, title, body, Table, Form, Script program segment, Applet, ActIveXControl ... all of these are embedded in HTML through <logo> </ logo>. HTML is a common language for various browsers, and all objects on the interface must be embedded in HTML to be interpreted by the browser.
3.1.2 CSS
For the translation of CSS, different domestic documents have different interpretations. The more common interpretation is "cascading style forms". The standard of the cascading style form is formulated by the W3C organization, and currently all browsers on the market generally support the CSS1 standard.
Cascading style forms define the display characteristics of a document element.
Each element contained in the HTML identifier can be defined to one or more content display settings. From a functional point of view, CSS can be subdivided into CSS1 / 2 and CSS-P (cascading style form positioning). The role of CSS1 / 2 is to set the display characteristics of document elements such as color and font; the role of CSS-P is to set the precise position of document elements on the page.
For creating a management information system for a medium-sized or large enterprise, such a large-scale Web Server-based system, using CSS is an ideal choice. It can effectively ensure that all pages present a unified display style, while also reducing a lot of coding work.
3.1.3 Script
Script refers to a certain scripting language. At present, there are two general scripting languages: JavaScript and VBScript. Since Netscape's Netscape does not support VBScript, JavaScript is the only option to write cross-browser scripts.
From a functional point of view, Script can be divided into client-side script and server-side script, because in the three-tier architecture, the server-side control and response is completed by Servlet and JSP, so the system only uses client-side script.
The main function of the client script is to check the rationality of the entered data and act as a filter to ensure that the data submitted to the Web Server is legal; combine business rules to control the display characteristics of interface elements; perform cookie operations when necessary .
3.1.4 Object
Object is a foreign object embedded in HTML. There are two commonly used Objects: Java Applet and MSAcTIveX Control. When the system's demand for interface flexibility and function exceeds the scope of HTML and Script, developers often consider Object technology.
Applet is a Java applet running on the client. It is downloaded to the client along with the page that contains it. It is interpreted and run by a browser that supports Java (with a Java virtual machine).
The function of AcTIveXControl is similar to Applet, the difference is that it can only run on the client of the Windows platform, and only download and install ActiveXControl the first time you access the page containing AcTIveX Control, until the ActiveXControl version of the server is upgraded Twice.
3.2 Middleware server The middleware server is composed of Web Server and Java ApplicationServer. Some middleware integrates these two parts together.
3.2.1 Web Server
HTTPServer uses a basic server architecture, which creates its own service processing thread pool at startup. The threads in the thread processing pool enter the loop, listen for HTTP requests from the client, and use the HTTP protocol to process the incoming HTTP requests. All HTTP connections are passed to them. After the HTTP request arrives, the service processing thread performs the necessary authorization check based on the URL and Server configuration information, decides which Servlet to call to process the request, and then returns the result of the Servlet processing to the client as a response.
There are several Servlets in the core position in the HTTP Server, they provide standard HTTP functions. These core Servlets are: File Servlet, used to process requests for file services, Cgi Servlet, which provides basic CGI functions, InvokerServlet, as a meta-servlet (meta-servlet), responsible for loading and activation of other Servlets And delete; Dispatcher Servlet: Separate partially trusted and fully trusted Servlets, so that they are executed in their own safe "sandbox".
There are many network application-level protocols, such as HTTP, FTP, SMTP, etc. Among them, the HTTP protocol is the most secure and the most widely used protocol, and HTTP requests are considered as safe requests by the firewall. Therefore, the three-tier structure middleware is provided with HTTPServer, which is the portal of the three-tier structure middleware, and is the bridge and link between the client and the Application Server that really handles business.
3.2.2 Java Application Server
Application Server is the core part of middleware and a service that truly implements business functions. It accepts the requests distributed by HTTPServer, makes corresponding processing, and then passes the processing results to HTTPServer, which forms HTTP responses and feeds back to the client.
3.2.3 Database server The database server is the carrier where the attributes of business objects can be permanently saved. The most direct way to ensure object persistence is to use an object-oriented database management system, which is specifically designed to store and share objects. At present, more relational databases used in large three-tier architecture application systems are Orcale, DB2, Sysbase, etc.
4 There are two camps of J2EE and Windows DNA to realize the classification three-tier structure system.
4.1 Implementation scheme based on Windows DNA structure If Windows DNA architecture is adopted, the database should consider Microsoft SQL Server. The SQLServer database is only suitable for small and medium-sized enterprises.
The advantage of using Windows DNA is that most desktop operating systems are currently Microsoft's Windows platform, and the office software we commonly use is also Microsoft products. This makes it easy to integrate e-commerce systems with daily office work. In addition, Microsoft's product prices are approachable. Moreover, Windows2000 not only comes with IISWeb server itself, but also fully integrates with COM +-middleware services, there is no need to choose the so-called "middleware" server. In addition, the use of Windows DNA structure, the development efficiency is more than 50% higher than the efficiency of using J2EE.
The disadvantage of using Windows DNA is that the system has poor platform compatibility and portability. This is well known and need not be repeated.
The implementation scheme based on Windows DNA structure is simply: ASP + ActiveX Control + COM + + ODBC.
4.2 Implementation Scheme Based on J2EE J2EE is an architecture that uses the Java 2 platform to simplify many complex problems related to the development, deployment, and management of multi-tier enterprise solutions. The foundation of J2EE technology is the standard version of the core Java platform or Java 2 platform. J2EE not only consolidates many of the advantages of the standard version, such as the "write once, run everywhere" feature, JDBC API for easy access to the database, CORBA technology and the ability to The security model for protecting data in Internet applications, etc., also provides comprehensive support for EJB (Enterprise JavaBeans), Java Servlets API, JSP (Java Server Pages) and XML technologies.
Sun added a complete set of core enterprise application programming interfaces to the Enterprise Edition, and all of these interfaces are standard modular components. J2EE technology also provides a complete set of enterprise services for these components, completes many time-consuming and laborious hard work in application development in an automated manner, and provides users with a way to create a widely compatible enterprise solution without complex programming platform. Taking advantage of this advantage, you can easily develop high-quality, enterprise-friendly applications, and you can greatly reduce product development time to market, costs, and risks.
In summary, the advantages of the J2EE architecture are:
Java Servlet and JSP must be compiled into Java Class to run as a Servlet, so the execution performance will be significantly improved.
Java Servlet and JSP can be completely programmed with Java, and can complete many simple business logics, especially JSP, which can directly write HTML, thus simplifying the output of the page, thus retaining the advantages of the scripting language is easy to use.
Complex business logic is deployed in EJBServer in the form of components. Because EJBServer provides a variety of component transaction services, the system is able to cope with a large number of concurrent users and manage complex transaction logic.
The component naming service integrated in EJBServer can make the location of components transparent, simplifying the deployment of components and the maintenance of client applications.
The development process is easy to divide the work, you can be responsible for writing components, and others assemble the page.
The J2EE platform fully supports and implements XML. This powerful combination enables XML to have cross-platform compatibility. Even tools for syntax checking and debugging of XML code can be platform independent. J2EE technology and XML technology are respectively the yin and yang poles of enterprise development, because XML can implement platform-independent data, while J2EE platform can implement platform-independent solutions. XML can represent data in a portable way, so it complements the portability of Java technology.
The realization scheme based on J2EE structure is: JSP + JavaBeans / EJB + Servlet + JDBC.
5 Implementation Case The author made an implementation case with Windows DNA:
In this case, the server station is built on Windows2000, and the database server uses SQLServer 6.5. A large amount of basic information of the unit is stored in the database, and users who have been identified can perform corresponding operations on these data according to their different needs, such as data reporting and query. Methods such as ASP and JavaScript are mainly used in the case.
5.1 Establishing a connection In order to establish a connection with a database, there are two ways: one is to establish DNS, and the other is OLE DB. Here we used DNS to create a SQL data source Convote. The parameters usually required for a DSN connection are: DSN name, user name, password, for example, we use the user name "users", password "pass", through DSN 
Connect to the database.
5.2 The user logs in, enters the user name and password, submits it, and obtains user information using the following statement: ![]()
After obtaining the user name and password and comparing it with the user name and password in the database, the correct one can enter the system, otherwise an error is prompted. 
5.3 Data query 

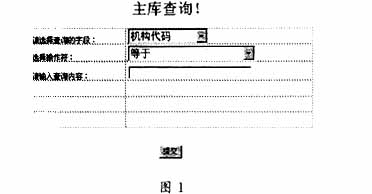
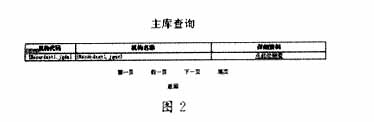
5.5 ActiveX control When the user's needs cannot be satisfied with Script, we often need to use Java Applet and MSActiveX control. Here, there is an example of MSActiveX control. ActiveX controls include additional support for host application display and operation components in the GUI environment, and you can also place OCX components in web pages.

For example, when the user needs to read and write the IC card on the client, because the reading and writing of the IC card is a more complicated program, this function cannot be realized simply by using Script statements. At this point we need to use ActiveX controls. I wrote an ActiveX OCX in VB, embedded it in HTML, and let the first-time user download along with the page. At the same time, the DLL that OCX calls is also downloaded to the client along with OCX, so the control can be executed on the client stand up.
Here we use the method of Asp page static call ActiveX control: ![]()
After that, you can use several methods of this ActiveX component in the ASP statement.
The card reading interface is shown in Figure 3.
Click to read the card, you can read the information in the card, as shown in Figure 4.

In short, the B / S model should be the future development direction.
Solar Security Light,Solar Led Flood Lights,Outdoor Solar Security Lights,300W Solar Flood Lights
Jiangmen Biaosheng Solar Energy Technology Co., Ltd. , https://www.bsprosolar.com